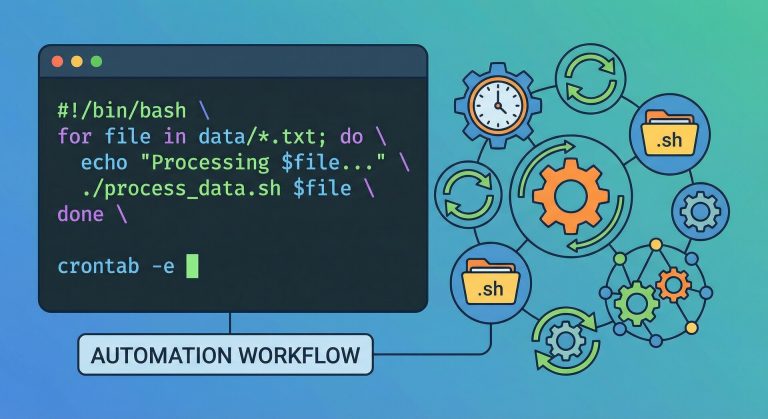
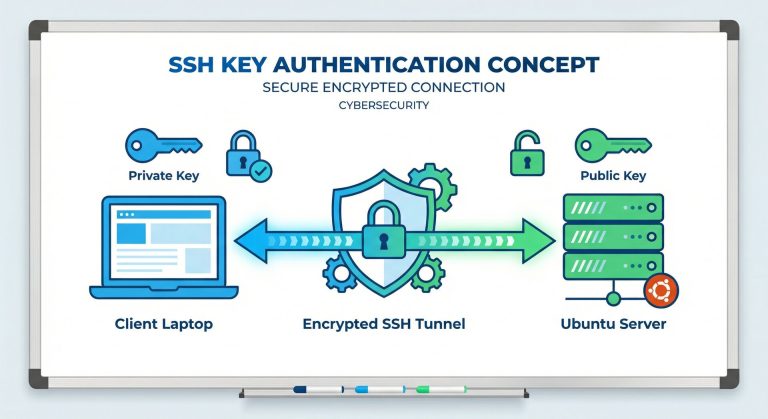
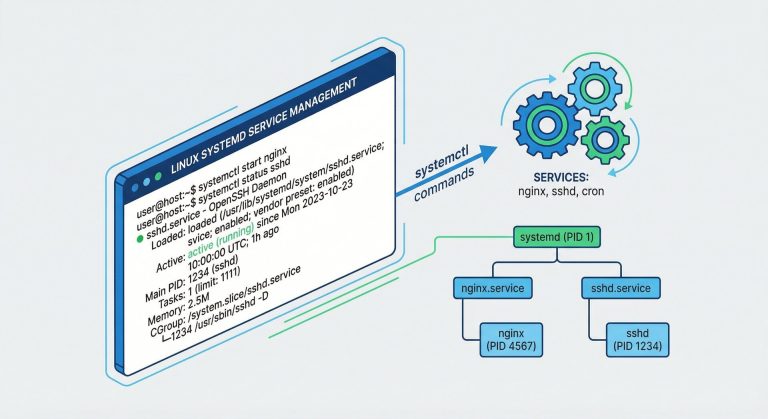
How to Set Up Ubuntu Server 2026: Complete Initial Configuration Guide

Complete Ubuntu server setup 2026 guide covering installation, SSH hardening, firewall configuration, security updates, Fail2Ban, and production-ready system hardening for Ubuntu 24.04 LTS.